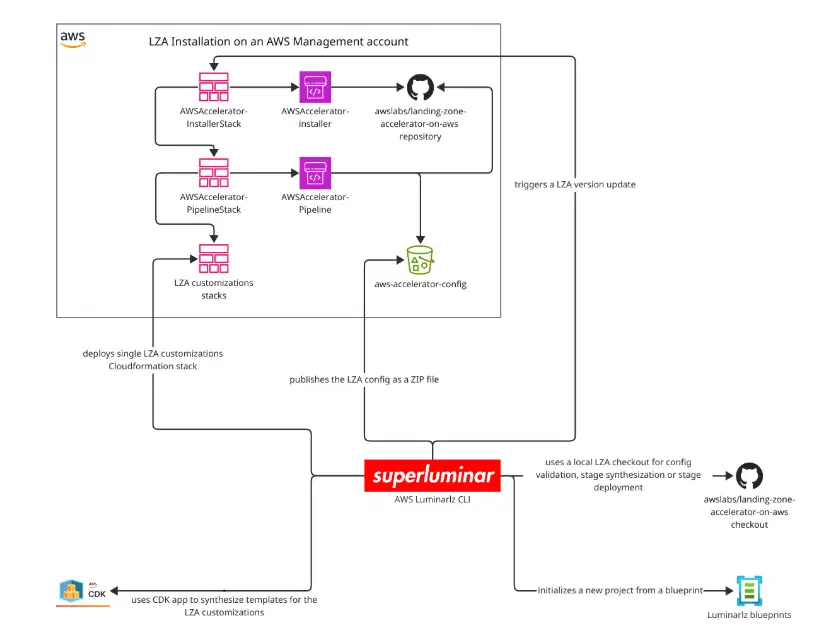
Introduction
After working extensively with the AWS Landing Zone Accelerator (LZA) in previous posts and hearing more buzz around alternative solutions like Nuvibit’s NTC (Nuvibit Terraform Collection), I decided to dive deep into both platforms. The question that kept coming up in client conversations was: “Which landing zone solution should we choose for our enterprise AWS deployment?”
Both solutions promise to accelerate cloud adoption, ensure compliance, and provide enterprise-grade infrastructure. But as we’ll see, they take fundamentally different approaches to achieving these goals. After deep-diving into their latest documentation and analyzing their architectural philosophies, I can now provide you with a more nuanced comparison that goes beyond surface-level features.
What became clear during this research is how these platforms embody different philosophies: LZA takes an AWS-native extensibility approach, while NTC focuses on developer experience and architectural patterns. Let me walk through what this means in practice.
The Challenge: Choosing Your Landing Zone Strategy
Setting up an enterprise-grade AWS environment is complex. You need:
- Multi-account governance and security controls
- Compliance with various frameworks (SOC 2, GDPR, PCI-DSS, etc.)
- Scalable networking architecture
- Centralized logging and monitoring
- Automated account provisioning and management
- Infrastructure that can evolve with your organization
The challenge isn’t just technical—it’s also about time to value, operational overhead, and long-term maintainability. This is where the choice between LZA and NTC becomes crucial.
AWS Landing Zone Accelerator: The Open Source solution directly from AWS
What is the LZA?
The AWS Landing Zone Accelerator is an open-source infrastructure as code (IaC) solution built with AWS CDK. It’s designed to sit on top of AWS Control Tower and extend its capabilities with additional security, compliance, and networking features.
From my experience working with LZA in production environments, here’s what stands out:
Architecture and Approach
- CDK-based: Built entirely on AWS CDK, which means TypeScript under the hood
- Configuration-driven: Uses 6-7 YAML configuration files to define your entire AWS organization
- Self-mutating pipeline: Deploys using AWS CodePipeline with automatic updates
- Control Tower first: AWS explicitly recommends deploying Control Tower as the foundational landing zone first, then enhancing with LZA
- Control Tower dependency: Designed to work on top of Control Tower’s existing organizational structure
Key Configuration Files
# The core configuration files that drive everything
├── accounts-config.yaml # Account creation and management
├── global-config.yaml # Global settings and logging
├── iam-config.yaml # IAM roles, policies, and permissions
├── network-config.yaml # VPC, Transit Gateway, networking
├── organization-config.yaml # OUs, SCPs, and governance
└── security-config.yaml # Security services and compliance
└── customizations-config.yaml # Custom CloudFormation stacks
What I Love About LZA
- Comprehensive coverage: Supports 35+ AWS services out of the box
- Compliance-ready: Built-in support for multiple compliance frameworks
- Open source: Full visibility into the code, active community
- AWS-native: Feels like a natural extension of AWS services
The Reality Check
But let’s be honest—LZA isn’t without its challenges. From my hands-on experience:
- Steep learning curve: The YAML configuration can become complex quickly
- Pipeline dependency: Everything runs through CodePipeline, which can be slow for iterations. Even a single change takes around 40 minutes. However the team is on it from the new experimental relase v1.13.0 on 💡
- Limited documentation: While improving, some configuration options lack detailed examples. Best is to use the sample configurations as guideline.
- Debugging complexity: When something fails, tracing through CDK + CloudFormation can be painful
Here are some redacted practical sampless of LZA configuration:
Account Creation (accounts-config.yaml):
mandatoryAccounts:
- name: Management
description: The management (primary) account. Do not change the name field for this mandatory account. Note, the account name key does not need to match the AWS account name.
email: <management-account>@example.com
organizationalUnit: Root
- name: LogArchive
description: The log archive account. Do not change the name field for this mandatory account. Note, the account name key does not need to match the AWS account name.
email: <log-archive>@example.com
organizationalUnit: Security
- name: Audit
description: The security audit account (also referred to as the audit account). Do not change the name field for this mandatory account. Note, the account name key does not need to match the AWS account name.
email: <audit>@example.com
organizationalUnit: Security
workloadAccounts:
# The "name" will be used to set the AWS Account name
# The "name" value does not currently support spaces
# The "name" value DOES NOT need to match the account name
- name: SharedServices
description: The SharedServices account
email: <shared-services>@example.com
organizationalUnit: Infrastructure
- name: Network
description: The Network account
email: <network>@example.com
organizationalUnit: Infrastructure
Network Configuration (network-config.yaml):
homeRegion: &HOME_REGION us-east-1
defaultVpc:
delete: true
excludeAccounts: []
transitGateways:
- name: Network-Main
account: Network
region: *HOME_REGION
shareTargets:
organizationalUnits:
- Infrastructure
asn: 65521
dnsSupport: enable
vpnEcmpSupport: enable
defaultRouteTableAssociation: disable
defaultRouteTablePropagation: disable
autoAcceptSharingAttachments: enable
routeTables:
- name: Network-Main-Core
routes: []
- name: Network-Main-Segregated
routes: []
- name: Network-Main-Shared
routes: []
- name: Network-Main-Standalone
routes: []
Security Controls (security-config.yaml):
homeRegion: &HOME_REGION us-east-1
centralSecurityServices:
delegatedAdminAccount: Audit
ebsDefaultVolumeEncryption:
enable: true
excludeRegions: []
s3PublicAccessBlock:
enable: true
excludeAccounts: []
scpRevertChangesConfig:
enable: true
snsTopicName: Security
macie:
enable: true
excludeRegions: []
policyFindingsPublishingFrequency: FIFTEEN_MINUTES
publishSensitiveDataFindings: true
guardduty:
enable: true
excludeRegions: []
s3Protection:
enable: true
excludeRegions: []
exportConfiguration:
enable: true
overrideExisting: true
destinationType: S3
exportFrequency: FIFTEEN_MINUTES
Nuvibit NTC: The Commercial Terraform Alternative
What is NTC?
Nuvibit’s Terraform Collection takes a different approach entirely. It’s a commercial, modular Terraform/OpenTofu toolkit designed for building enterprise-grade AWS infrastructure with a focus on developer experience and operational efficiency.
From examining their documentation, NTC is built around the Nuvibit AWS Reference Architecture (NARA), which they describe as refined through multiple real-world implementations. This architectural foundation differentiates it from generic Terraform modules. See here for more details.
Architecture and Philosophy
- Terraform-native: Built entirely on Terraform/OpenTofu
- AWS Organizations first: Prefers working directly with AWS Organizations rather than Control Tower
- Control Tower as beta: While Control Tower support exists, it’s considered beta/experimental
- Modular building blocks: 5 core areas (Cloud Management, Security, Connectivity, Operations, Templates)
- Professional services included: Comes with implementation support and knowledge transfer
- Internal Developer Platform (IDP) focus: Emphasizes developer productivity tools
- NARA foundation: Built on the Nuvibit AWS Reference Architecture for enterprise-grade reliability
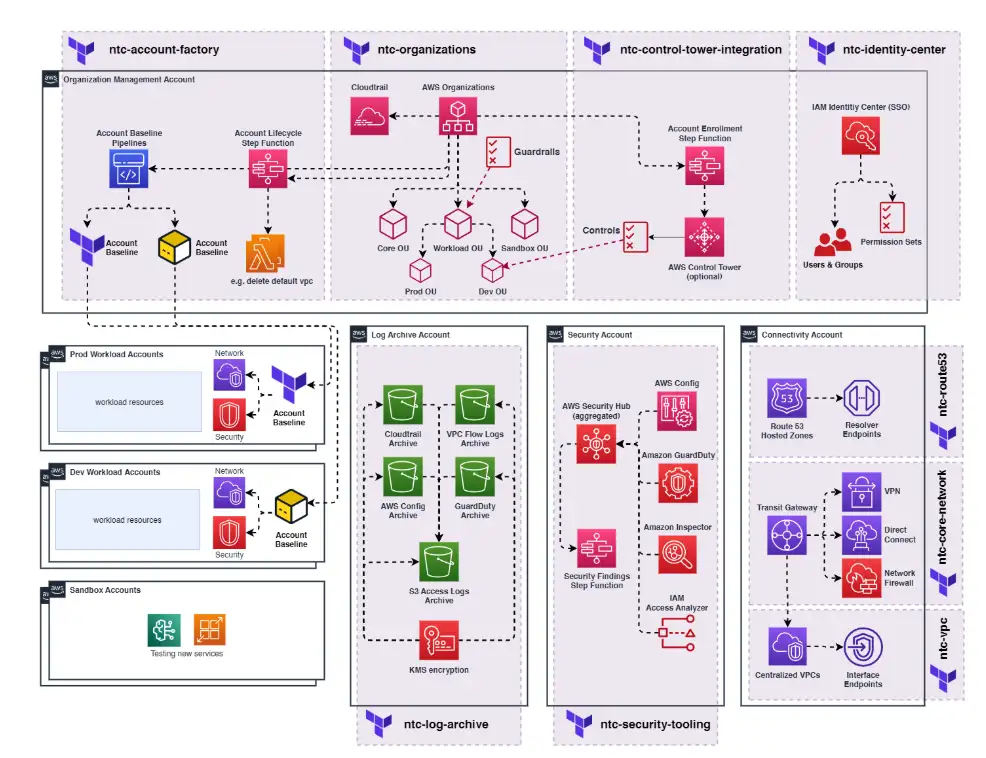
The Five Core Building Blocks
Diving deeper into NTC’s architecture, I discovered these aren’t just arbitrary groupings—they map directly to what Nuvibit calls their “core accounts” in NARA. Here’s what each building block actually provides:
Cloud Management (⚙️)
- NTC Organizations: Direct AWS Organizations management with delegated administrators
- NTC Account Factory: Automated account provisioning with customizable baselines and lifecycles
- NTC Identity Center: Permission sets, prerequisites, and centralized access management
- NTC Parameters: Cross-account parameter sharing for configuration consistency
- NTC Control Tower Integration: Beta support for existing Control Tower environments
Security (🛡️)
- NTC Security Tooling: Centralized Security Hub, Config, GuardDuty, and Inspector management
- NTC Log Archive: Centralized S3 buckets for CloudTrail, VPC Flow Logs, and audit data
- Automation Rules: Custom security response automation for Security Hub findings
- Central Configuration Policies: Standardized security configurations across accounts
Connectivity (🌐)
- NTC Core Network: Transit Gateway, Network Firewall, and inter-region connectivity
- NTC VPC: Standardized VPC patterns with automated subnet calculations
- NTC IPAM: IP Address Management for conflict-free CIDR allocation
- NTC Route53: DNS management and private hosted zones
Operations (🛠️)
- NTC Administration (GitHub/Spacelift): Comprehensive CI/CD platform management for Infrastructure as Code deployments. This module automates Spacelift environment setup including stack creation, role-based access control (RBAC), Open Policy Agent (OPA) policy integration, and secure pipeline authentication. It supports both Spacelift SaaS and self-hosted deployments, with built-in drift detection, state management, and policy-as-code enforcement
- Observability (coming soon): Centralized monitoring and alerting
- Backup Management (coming soon): Cross-account backup orchestration
Templates (📄)
- NTC Account Baseline Templates: Foundational configurations for new accounts
- NTC Account Lifecycle Templates: Automation for account creation, modification, and decommissioning
- NTC Guardrail Templates: Service Control Policies and compliance frameworks
What Caught My Attention
NARA’s Architectural Foundation: The reference architecture whitepaper reveals substantial thought behind NTC’s design. NARA addresses scalability, compliance, and enterprise reliability patterns based on their documented experience with AWS foundations.
Multi-Account Design: NARA is architected from the start for account separation rather than retrofitted. Their Core Accounts approach (Organization Management, Log Archive, Security Tooling, Connectivity, plus optional Monitoring/Backup) reflects experience with enterprise AWS patterns.
Developer Experience: NTC seems laser-focused on making life easier for development teams. The documentation emphasizes “Internal Developer Platforms” and “end-to-end automation”—concepts that resonate with modern DevOps practices.
Professional Services: Unlike LZA, NTC comes with a structured 6-step implementation process:
- Initial contact and demo
- Contract signing
- Kickoff workshop
- Initial setup and integration
- Deployment assistance
- Knowledge transfer and go-live support
Compliance Integration: NARA includes support for ISO 27001, GDPR, and HIPAA as architectural components rather than add-on features.
Terraform Ecosystem: For organizations already invested in Terraform, this could be a natural fit.
NTC Code Examples
Based on the documentation, here’s how NTC approaches similar configurations:
Account Management with Terraform: see https://docs.nuvibit.com/ntc-building-blocks/management/ntc-account-factory/ for more details:
# --------------------------------------------------------------------------------------------------
# ¦ NTC ACCOUNT FACTORY
# --------------------------------------------------------------------------------------------------
module "ntc_account_factory" {
source = "github.com/nuvibit-terraform-collection/terraform-aws-ntc-account-factory?ref=X.X.X"
# this bucket stores required files for account factory
account_factory_baseline_bucket_name = "ntc-account-factory-baseline"
# this bucket stores required cloudtrail logs for account factory
account_factory_cloudtrail_bucket_name = "ntc-account-factory-cloudtrail"
# increase quotas for aws services used in account factory
increase_aws_service_quotas = {
codebuild_concurrent_runs_arm_small = 20
}
# account names and emails cannot be changed without manual intervention - set naming conventions to avoid mistakes
account_factory_naming_conventions = {
account_name_regex = "^aws-c2-[a-z0-9-]+$"
account_email_regex = "@nuvibit.com$"
}
# and more...
}
Network Infrastructure: see https://docs.nuvibit.com/ntc-building-blocks/connectivity/ntc-core-network/ for more details:
# --------------------------------------------------------------------------------------------------
# ¦ NTC CORE NETWORK
# --------------------------------------------------------------------------------------------------
module "ntc_core_network_frankfurt" {
source = "github.com/nuvibit-terraform-collection/terraform-aws-ntc-core-network?ref=X.X.X"
# ------------------------------------------------------------------------------------------------
# ¦ TRANSIT GATEWAY
# ------------------------------------------------------------------------------------------------
transit_gateway = {
name = "tgw-core-frankfurt"
description = "core network in frankfurt"
amazon_side_asn = 64512
default_route_table_association = false
default_route_table_propagation = false
dns_support = true
multicast_support = false
vpn_ecmp_support = true
security_group_referencing_support = true
cidr_blocks = []
route_table_names = [
"tgw-core-rtb-hub",
"tgw-core-rtb-spoke-prod",
"tgw-core-rtb-spoke-dev",
"tgw-core-rtb-spoke-int",
"tgw-core-rtb-onprem",
]
# (optional) share subnet with Organizations, OUs or Accounts - requires RAM to be enabled for Organizations
auto_accept_shared_attachments = true
ram_share_principals = [
local.ntc_parameters["mgmt-organizations"]["ou_ids"]["/root/workloads"]
]
ram_share_allow_external_principals = false
}
# and more...
Security Baselines: see https://docs.nuvibit.com/ntc-building-blocks/security/ntc-security-tooling/ for more details:
# --------------------------------------------------------------------------------------------------
# ¦ NTC SECURITY TOOLING
# --------------------------------------------------------------------------------------------------
module "ntc_security_tooling" {
source = "github.com/nuvibit-terraform-collection/terraform-aws-ntc-security-tooling?ref=X.X.X"
# set to true to enable securityhub standards that securityhub has designated as automatically enabled
# use 'securityhub_central_configuration_polices' to configure security standards across entire aws organizations
enable_securityhub_default_standards = false
# securityhub aggregration is required for central configuration
enable_securityhub_central_configuration = true
enable_securityhub_aggregation = true
# can be either "ALL_REGIONS" or a list of regions which should be aggregated
# this will also apply the central configuration policies to the specified regions
securityhub_aggregation_regions = [
# "eu-central-1", current region must be excluded from this list
"eu-central-2",
"us-east-1"
]
# (optional) aggregate config data from all accounts in all regions across organizations
# admin delegation for "config.amazonaws.com" required
# https://docs.aws.amazon.com/config/latest/developerguide/aggregate-data.html
enable_config_aggregation = false
# enrich securityhub findings with account context
securityhub_enrichment_settings = {
enable_enrichment = true
# enrich only findings of specific severity from ["INFORMATIONAL", "LOW", "MEDIUM", "HIGH", "CRITICAL"]
severity_labels = ["INFORMATIONAL", "LOW", "MEDIUM", "HIGH", "CRITICAL"]
# to get alternate contact an assumable iam role is required in the org management account
alternate_contact_assume_role = "ntc-org-account-reader"
}
# and more...
The High level Comparison
Let me break down the key differences based on what matters most in enterprise deployments:
Implementation Approach
| Aspect | AWS LZA | Nuvibit NTC |
|---|---|---|
| Technology Stack | AWS CDK (TypeScript) | Terraform/OpenTofu |
| Configuration | YAML files | HCL (Terraform) |
| Deployment | CodePipeline | Terraform workflows |
| CI/CD Platform | AWS CodePipeline + CodeCommit | Native Spacelift integration with GitHub/GitLab |
| GitOps Approach | Self-mutating pipeline | Purpose-built IaC platform with drift detection |
| Extensibility | Custom CDK constructs | Terraform modules |
| Organizational Management | Control Tower first (required) | AWS Organizations first (Control Tower beta) |
Organizational Management: A Key Architectural Difference
This is where the two platforms diverge significantly, and the architectural differences have practical implications:
AWS LZA requires Control Tower as its foundation. From the documentation, AWS explicitly states the recommendation: “Deploy Control Tower first in your AWS organization” as the foundational landing zone, then enhance with LZA. You must:
- Deploy Control Tower first in your AWS organization
- Set up the basic organizational structure through Control Tower
- Then deploy LZA on top to enhance and extend capabilities
This means you get Control Tower’s benefits (automated account factory, guardrails, dashboard) but also its constraints and additional complexity. It’s a layered architecture approach.
Nuvibit NTC takes what I’d call the foundational architecture approach:
- Works directly with AWS Organizations API through NTC Organizations
- Manages accounts, OUs, and SCPs through Terraform with granular control
- Centralized root access management and delegated administrators built-in
- Control Tower support exists but is marked as beta/experimental—they clearly see it as optional
- Organizational policies (SCPs) are first-class citizens, not add-ons
NTC’s approach treats organizational structure and organizational policies as foundational elements, while LZA positions them as enhancements to Control Tower’s base setup.
This difference impacts everything from initial setup to long-term management workflows.
CI/CD and GitOps: Two Different Philosophies
Another critical architectural difference lies in how each platform approaches continuous deployment and GitOps workflows:
AWS LZA: Native AWS CI/CD
- Uses AWS CodePipeline with self-mutating capabilities
- Configuration changes trigger automatic pipeline runs
- State managed through AWS CloudFormation stacks
- Git integration via AWS CodeCommit (though GitHub integration and an S3 bucket are possible as well)
- Pipeline mutations allow the infrastructure to update its own deployment process
NTC: Purpose-Built IaC Platform Integration
- Deep Spacelift integration with automated stack management
- Native GitHub and GitLab integration for source control
- Open Policy Agent (OPA) for policy-as-code enforcement
- Built-in drift detection and remediation capabilities
- Role-based access control (RBAC) for team collaboration
- Support for both Spacelift SaaS and self-hosted deployments
The NTC approach leverages what their documentation calls “purpose-built CI/CD tools for IaC” — platforms designed specifically for infrastructure workflows rather than generic CI/CD systems adapted for infrastructure use. This includes features like:
- Infrastructure state visualization and management
- Policy enforcement at deployment time
- Cross-stack dependency management
- Automated compliance reporting
This architectural choice reflects NTC’s focus on developer experience and operational efficiency for infrastructure teams, while LZA maintains closer integration with native AWS services.
Deep Dive: Core Account Architectures
After analyzing both platforms’ documentation, I found their approaches to core accounts reveal fundamental architectural philosophies. Let me break down what I discovered:
LZA’s Approach: Control Tower + Enhancements
LZA builds on Control Tower’s foundation accounts:
- Management Account: Control Tower’s organizational root
- Audit Account: Control Tower’s compliance and logging hub
- Log Archive Account: Control Tower’s centralized logging
Then LZA enhances this with additional capabilities through its configuration files:
- Security services across all accounts via
security-config.yaml - Networking through
network-config.yaml(VPCs, Transit Gateways, etc.) - Custom infrastructure via
customizations-config.yaml
This is an additive model—you get Control Tower’s opinionated structure, then layer on LZA’s capabilities.
NTC’s Approach: Purpose-Built Core Accounts
NARA defines core accounts from first principles, each with specific responsibilities:
Organization Management Account:
- AWS Organizations management
- Account factory and lifecycle automation
- Identity Center integration
- Cross-account parameter management
Security Tooling Account:
- Centralized Security Hub aggregation
- GuardDuty, Config, and Inspector management
- Automation rules for security findings
- IAM Access Analyzer and compliance monitoring
Log Archive Account:
- S3 buckets for CloudTrail, VPC Flow Logs, GuardDuty findings
- KMS encryption for audit data
- Cross-account log delivery and retention
Connectivity Account:
- Transit Gateway and inter-region networking
- Network Firewall for traffic inspection
- Route 53 DNS management
- IPAM for IP address conflict resolution
Optional Specialized Accounts:
- Monitoring Account: Centralized observability (CloudWatch, X-Ray, third-party integrations)
- Backup Account: Cross-account backup orchestration with AWS Backup
NTC’s approach assigns specific responsibilities to each account, while LZA distributes capabilities across the Control Tower foundation.
The Architectural Philosophy Difference
LZA: “Start with AWS best practices (Control Tower), then enhance with additional capabilities”
- ✅ Leverages AWS’s opinionated foundation
- ✅ Inherits Control Tower’s governance and dashboards
- ❌ Bound by Control Tower’s structural decisions
- ❌ Configuration spread across YAML files can become complex
NTC: “Design optimal account structure from first principles, then implement with proven patterns”
- ✅ Purpose-built accounts with clear responsibilities
- ✅ Granular control over organizational structure
- ✅ Compliance and security designed-in from day one
- ✅ Customizations are easier to realize
- ❌ More upfront architectural decisions required. However NARA gives a very good blueprint.
- ❌ Little less alignment with AWS’s “standard” patterns
This architectural difference explains why NTC’s Control Tower support remains experimental—the approaches have fundamentally different design principles.
Configuration Complexity Comparison
Let’s look at how both handle a common scenario: Setting up organizational units with SCPs
LZA Approach (organization-config.yaml):
enable: true
organizationalUnits:
- name: Security
- name: Infrastructure
quarantineNewAccounts:
enable: true
scpPolicyName: Quarantine
serviceControlPolicies:
- name: AcceleratorGuardrails1
description: >
Accelerator GuardRails 1
policy: service-control-policies/guardrails-1.json
type: customerManaged
deploymentTargets:
organizationalUnits:
- Infrastructure
- Security
NTC Approach (main.tf):
module "ntc_organizations" {
source = "github.com/nuvibit-terraform-collection/terraform-aws-ntc-organizations?ref=X.X.X"
# Other configuration...
organization_policies = [
# Reference a policy from guardrail templates
module.ntc_guardrail_templates.service_control_policies["scp_root_ou"],
# Or define a custom policy
{
policy_name = "custom_scp_policy"
policy_type = "SERVICE_CONTROL_POLICY"
target_ou_paths = ["/root/workloads"]
target_account_ids = []
policy_json = jsonencode({
Version = "2012-10-17"
Statement = [
{
Sid = "DenyUnencryptedObjectUploads"
Effect = "Deny"
Action = "s3:PutObject"
Resource = "*"
Condition = {
StringNotEquals = {
"s3:x-amz-server-side-encryption" = "AES256"
}
}
}
]
})
}
]
}
Cost Structure
AWS LZA:
- ✅ Free and open source
- ✅ Only pay for AWS services used
- ❌ Internal implementation costs can be high
Nuvibit NTC:
- ❌ Commercial licensing (pricing not publicly available)
- ✅ Includes professional services
- ✅ Potentially faster time-to-value
Learning Curve and Expertise
From my experience, here’s the reality:
AWS LZA requires:
- Deep AWS knowledge
- CDK/CloudFormation understanding
- YAML configuration expertise
- CodePipeline troubleshooting skills
Nuvibit NTC requires:
- Terraform/OpenTofu proficiency
- AWS foundational knowledge
- Less AWS-specific deep diving (due to abstraction)
Operational Considerations
Updates and Maintenance
LZA: Manual updates through CodePipeline, requires careful planning for version upgrades
NTC: Terraform state management, potentially more granular control over changes
Debugging and Troubleshooting
LZA: CloudFormation stack traces, CDK synthesis debugging
NTC: Terraform plan/apply output, more transparent change management
Customization
LZA: Custom CDK constructs, CloudFormation templates
Example LZA Customization (customizations-config.yaml):
customizations:
cloudFormationStacks:
- deploymentTargets:
accounts:
- Production
template: templates/custom-monitoring.yaml
name: CustomMonitoring
parameters:
- name: Environment
value: prod
- name: AlertEmail
value: alerts@mycompany.com
cloudFormationStackSets:
- deploymentTargets:
organizationalUnits:
- Workloads
template: templates/backup-policy.yaml
name: BackupPolicy
capabilities: [CAPABILITY_IAM]
regions:
- eu-central-1
NTC: via custom Terraform modules, which are potentially more flexible due to Terraform’s ecosystem
When to Choose Which?
Based on my analysis and real-world experience, here’s my recommendation:
Choose AWS LZA if:
- You’re already deep in the AWS ecosystem
- Budget constraints are tight (open source)
- You have strong CDK/CloudFormation expertise in-house
- You want maximum control over the implementation
- Control Tower integration is important
- You can invest time in the learning curve
Choose Nuvibit NTC if:
- Your team is already Terraform-native
- You value professional services and support
- Time-to-market is critical
- You want to minimize internal AWS expertise requirements
- Developer experience is a top priority
- Budget allows for commercial solutions
- You operate in regulated industries (NARA includes compliance patterns)
- You prefer account-specific architecture over Control Tower’s structure
- You want foundational rather than additive architecture
Real-World Implementation Insights
LZA in Practice
From my previous posts about daily working with LZA and using the LZA, the main operational challenges I’ve encountered:
- Pipeline failures: When something breaks, it often breaks spectacularly
- Configuration complexity: The YAML files can become unwieldy
- Update cycles: Changes require full pipeline runs, which can be time-consuming
But the benefits are real:
- Cost efficiency: Running a full LZA setup for around $150/month
- Compliance coverage: Built-in support for major frameworks
- Community support: Active GitHub community and AWS backing
NTC Considerations
While I haven’t deployed NTC in production yet, diving deeper into their documentation reveals both strengths and considerations:
Strengths:
- Architectural foundation: NARA provides documented patterns from multiple implementations
- Compliance integration: Designed with regulatory requirements as architectural components
- Modular approach: Each building block can be implemented independently
- Terraform state management: Potentially better change visibility than CloudFormation
- Professional services: 6-step implementation process with knowledge transfer
- Core account separation: Sophisticated multi-account patterns baked in
- Developer experience focus: Internal Developer Platform concepts throughout
Considerations & Unknowns:
- Commercial licensing: Pricing not publicly available—could be significant for large organizations
- Vendor dependency: While Terraform-based, the modular approach creates dependency on Nuvibit’s specific implementations
- Community ecosystem: Smaller community compared to AWS’s open-source LZA
- Control Tower integration: Still marked as “beta/experimental” which could limit adoption
- Update cycles: How frequently are modules updated? What’s the upgrade path?
- Roadmap alignment: How well does Nuvibit’s development track with AWS service changes?
What I’d want to test:
- Deployment speed: Does the professional services model actually accelerate time-to-value?
- State management: How complex does the Terraform state become at enterprise scale?
- Customization limits: Where do you hit the boundaries of the modular approach?
- Operational overhead: Day-to-day management compared to LZA’s CodePipeline approach
The Verdict: It Depends (But Here’s My Take)
After diving deep into both solutions, here’s my honest assessment:
For most enterprises starting fresh: I’d lean toward AWS LZA if you have the AWS expertise in-house and can invest in the learning curve. The open-source nature, comprehensive feature set, and zero licensing costs make it compelling for long-term sustainability.
For Terraform-native organizations: Nuvibit NTC could be the better choice, especially if you value professional services and faster implementation. The modular approach aligns well with modern IaC practices.
For rapid deployment needs: NTC might win due to the included professional services, NARA’s architectural maturity, and potentially smoother implementation process.
For compliance-focused organizations: NTC’s NARA includes regulatory frameworks (ISO 27001, GDPR, HIPAA) as architectural components, while LZA requires additional compliance configuration (which is also provided as a separate landing-zone-accelerator-on-aws-for-healthcare sample configuration).
For GitOps-focused teams: NTC excels with its Spacelift administration capabilities, offering purpose-built IaC CI/CD workflows, policy-as-code enforcement, drift detection, and advanced collaboration features that generic CI/CD platforms struggle to match.
What I’m Planning Next
After this deep dive into both platforms’ documentation, I’m more convinced than ever that a hands-on comparison is needed. I’m considering setting up a side-by-side implementation to test both solutions with identical enterprise requirements.
Specific areas I want to explore:
- Architecture deployment: NARA’s core accounts vs. LZA’s Control Tower + enhancements approach
- Compliance implementation: How each handles GDPR, ISO 27001, and custom compliance frameworks
- Operational workflows: NTC’s Terraform state management vs. LZA’s CodePipeline mutations
- Customization boundaries: Where do you hit limits in each platform’s modularity?
- Developer experience: Which actually delivers on the “Internal Developer Platform” promise?
- Cost implications: Total cost of ownership including licensing, operational overhead, and professional services
The documentation suggests some architectural differences that I’d love to validate in practice. For instance, does NTC’s “foundational architecture” approach really provide more flexibility than LZA’s “layered architecture” model?
This could make for a comprehensive follow-up series if there’s interest from the community—perhaps even a challenge implementing the same enterprise requirements in both platforms.
Conclusion
Both AWS LZA and Nuvibit NTC are serious enterprise solutions for AWS landing zone implementation, but this deep dive reveals they embody fundamentally different architectural philosophies. The choice ultimately depends on your organization’s expertise, budget, timeline, compliance requirements, and architectural preferences.
AWS LZA remains my go-to recommendation for AWS-native organizations with the technical capacity to manage it effectively. The layered architecture approach (Control Tower + enhancements) provides a familiar foundation with extensive customization capabilities. The cost savings alone can be significant over time, but the operational complexity shouldn’t be underestimated.
Nuvibit NTC offers a more comprehensive approach than I initially expected. The foundational architecture through NARA demonstrates solid understanding of enterprise AWS patterns. For organizations prioritizing compliance, developer experience, and professional support—particularly those using Terraform—it provides a viable alternative with potentially faster implementation.
The key insight: these represent different approaches to cloud governance, not just different toolsets. Your choice should align with your architectural preferences and organizational needs.
What’s your experience with either solution? Have you evaluated both? I’d love to hear your thoughts and real-world insights.
And if you want a short 13min summary how NTC changed the platform philosophy at the Swiss government, take a look here 👇
Resources for Further Reading
AWS LZA:
- Official documentation
- AWS Solutions
- AWS Prescriptive Guidance Landing Zone
- GitHub repository
- My previous posts on setting up, using LZA, daily working with the LZA part 1 and part 2
Nuvibit NTC:
Like what you read? You can hire me 💻, book a meeting 📆 or drop me a message to see which services may help you 👇