Introduction
In previous posts such as setting up the LZA, using the LZA and daily work with the LZA, we elaborated next to the setup and usage of the LZA also using it at a daily basis. In this post, we will go on with even more daily usage/admin task and customizations, such as
- Using autocompletion for the LZA config files
- Updating procedures
- Removing accounts from LZA
Let’s get started and get into the details!
Using autocompletion
Autocompletion within the LZA was first introduced in v1.10.0. Take a look at the docs here. I found this quite interesting and also contributed a minor documentation improvement. You can find the PR here.
This improves the developer experience a lot:
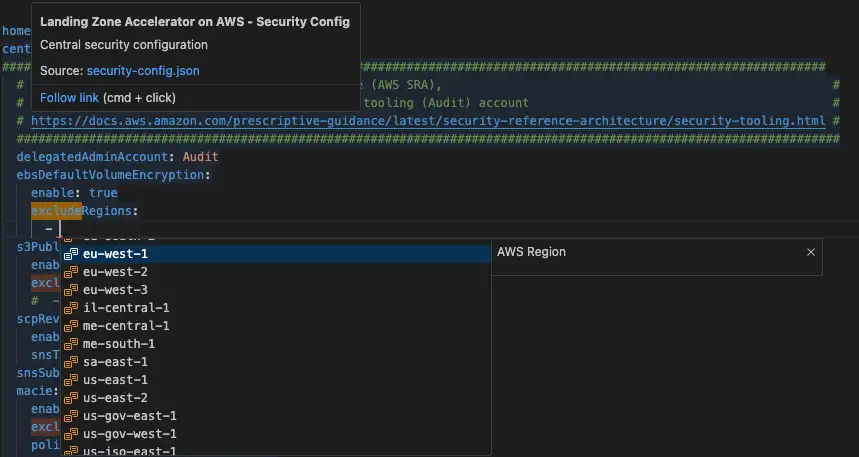
Checking updates of the config and docs
To start it off I first run the following commands to compare the updates from my current version to the new version. This gives me a good overview of what needs to be adapted.
Nothing special, just comparing to documentation and the current configuration I used as a baseline:
export lza_from_version=v1.10.0
export lza_to_version=v1.11.2
cd landing-zone-accelerator-on-aws
git pull origing main
git checkout $lza_to_version
cd source/
yarn
yarn validate-config ../../aws-accelerator-config/
cd ..
# configs
git diff $lza_from_version..$lza_to_version reference/sample-configurations/lza-sample-config/
# docs for new features
git diff $lza_from_version..$lza_to_version source/mkdocs/docs/
After I have an overview, I know where to continue when updating to a new version.
Removing accounts from LZA
Sometimes it’s also necessary that you want to remove accounts from the LZA. I mean to be precise accounts, which are under control of the LZA and controltower.
This is usually my workflow:
- I move accounts to Suspended OU in
accounts-config.yamlfile, e.g. the account namedEventSandbox1in this example:
# omitted for brevity...
workloadAccounts:
- name: EventSandbox1
description: The SEventSandbox1 account
email: root+eventsandbox-45sd2s2y@aws.mycompany.com
organizationalUnit: Suspended
# others ...
As a reminder the organization-config.yaml look as follows:
enable: true
organizationalUnits:
- name: Security
- name: Infrastructure
- name: Production
- name: Development
- name: Public
- name: Sandbox
- name: Suspended
ignore: true
which means tha the Suspended OU is not managed by the LZA. So account within this OU should not have the cloudformation stacks installed coming from LZA. However, when we want remove an account which was previously under the control of the LZA, we have to manually uninstall the stacks. This comes now
- I use the following script, which has the advantage that the
$lza_mgmt_role, this caseAWSControlTowerExecution, is not restricted by the LZA SCPs.
#!/bin/bash
set -eo pipefail
aws_account_region=eu-central-1 # <- edit here
parent_ou_to_remove_lza_accounts_from=ou-xxx-yyyy233yy # <- edit here
lza_mgmt_role=AWSControlTowerExecution # assuming you installed via Controltower
# login to your management account via https://granted.dev/
# or any other tool of your choice
assume mgmt-account
# 1. list all account of the ou
aws organizations list-accounts-for-parent \
--parent-id $parent_ou_to_remove_lza_accounts_from \
--no-cli-pager > lza_accounts_to_remove.json
max_account_count=$(jq '.Accounts | length' lza_accounts_to_remove.json)
echo "Found $max_account_count accounts in the parent_ou_to_remove_lza_accounts_from"
# 2. terminate the CT product for each account
count=0
jq -c '.Accounts[].Id' lza_accounts_to_remove.json | while read i; do
count=$((count+1))
account_id=$(echo $i | sed -e 's/^"//' -e 's/"$//')
echo "($count/$max_account_count) cleaning account '$account_id' from LZA stacks"
# assume role AWSControlTowerExecution in this account
aws sts assume-role --role-arn arn:aws:iam::$account_id:role/$lza_mgmt_role \
--role-session-name remove-events-account-lza-only > assume-role-credentials.json
# only LZA stacks starting with 'AWSAccelerator'
AWS_ACCESS_KEY_ID=$(jq -r '.Credentials.AccessKeyId' assume-role-credentials.json) \
AWS_SECRET_ACCESS_KEY=$(jq -r '.Credentials.SecretAccessKey' assume-role-credentials.json) \
AWS_SESSION_TOKEN=$(jq -r '.Credentials.SessionToken' assume-role-credentials.json) \
aws cloudformation describe-stacks \
--query "Stacks[?starts_with(StackName, 'AWSAccelerator')].StackId" > stackIds.json
# log amount of stacks
stack_count=$(jq '. | length' stackIds.json)
echo "Found $stack_count stacks in account '$account_id'"
# disable termination protection for each stack
jq -c '.[]' stackIds.json | while read i; do
stackId=$(echo $i | sed -e 's/^"//' -e 's/"$//')
echo "In account '$account_id' disabling termination protection for stack '$stackId'"
AWS_ACCESS_KEY_ID=$(jq -r '.Credentials.AccessKeyId' assume-role-credentials.json) \
AWS_SECRET_ACCESS_KEY=$(jq -r '.Credentials.SecretAccessKey' assume-role-credentials.json) \
AWS_SESSION_TOKEN=$(jq -r '.Credentials.SessionToken' assume-role-credentials.json) \
aws cloudformation update-termination-protection \
--no-enable-termination-protection \
--stack-name $stackId
# delete the stack
echo "In account '$account_id' deleting stack '$stackId'"
AWS_ACCESS_KEY_ID=$(jq -r '.Credentials.AccessKeyId' assume-role-credentials.json) \
AWS_SECRET_ACCESS_KEY=$(jq -r '.Credentials.SecretAccessKey' assume-role-credentials.json) \
AWS_SESSION_TOKEN=$(jq -r '.Credentials.SessionToken' assume-role-credentials.json) \
aws cloudformation delete-stack --stack-name $stackId --no-cli-pager
echo "Waiting 5s before next stack"
sleep 5
done
done
Of course, you can also do this manually via the console. Up to you.
Conclusion
In this post, we talked more bout the daily usage of the LZA and more admin tasks. Some topics were only touched briefly as more in-depth blog posts are linked and more will come.
Like what you read? You can hire me 💻, book a meeting 📆 or drop me a message to see which services may help you 👇